Description
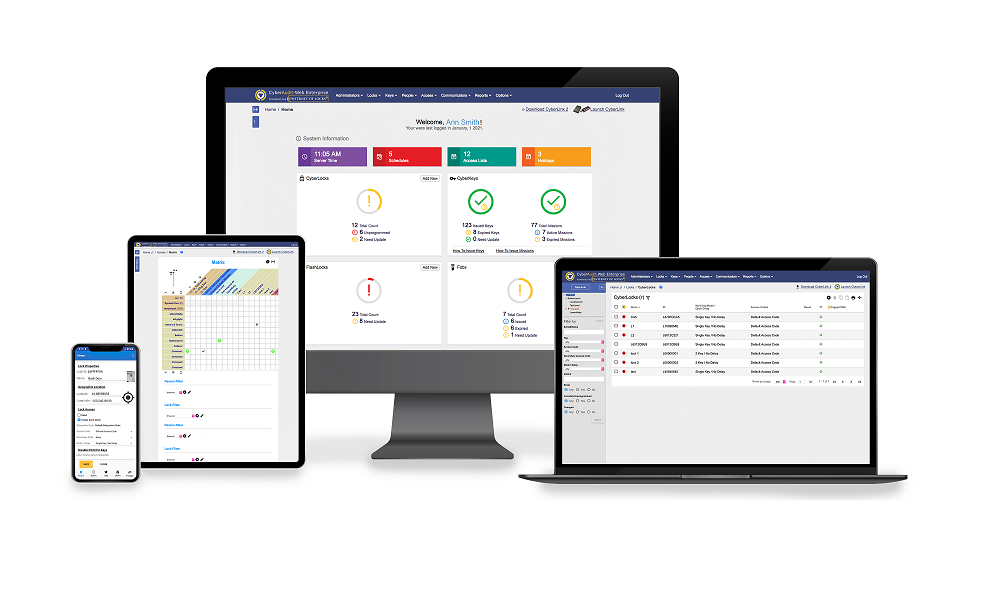
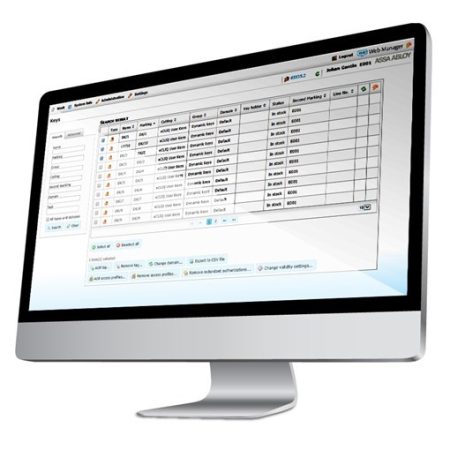
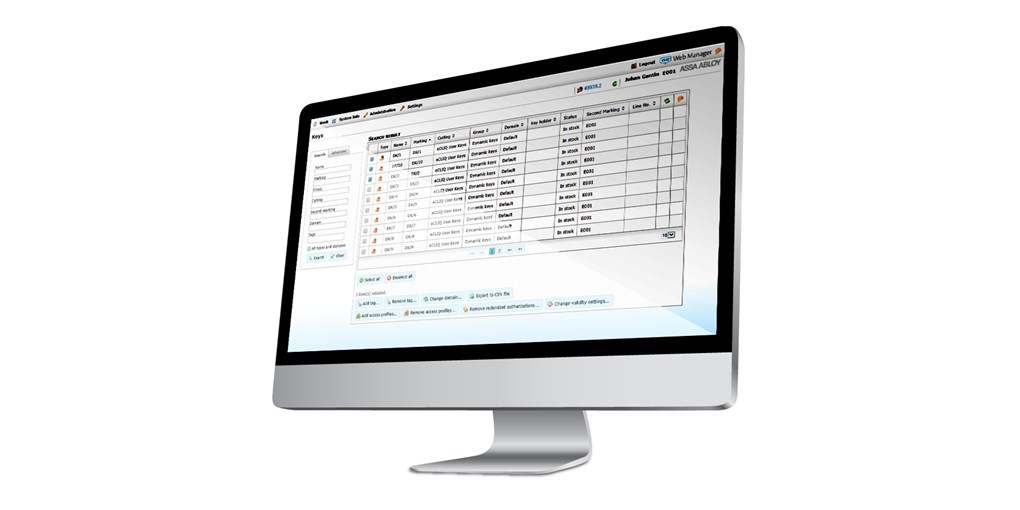
CyberAudit Web Software
A web-based application designed to simplify the management of your CyberLock security system.
This software is available as a self hosted application or a fully supported and managed cloud based solution. A hierarchy of administrators allows individual managers responsibility for only the CyberLocks and the people in their area. It even manages assets across countries and time zones.
An intuitive point-and-click browser-based interface that uses drop-down information boxes is all that’s needed to access the modules that drive EKA CyberLock’s access control, monitoring and reporting capabilities.